No matter how big & beautiful you make your kingdom, you can’t rule for long if you can’t secure it. We don’t know who told this, but this is appropriate for almost all the businesses today. Especially in IT industry, app security is something which should lead the priority list. It is not because people are afraid of this so called threat of internet, but in reality no one would like to take any chance when it comes to Business Data Security.
So to put some light on this topic, we are going to discuss few very important security practices that need to be taken care when you are developing a mobile application for your business.
During the development process of any kind of application, almost everyone follows certain pre-defined methods for development and same goes for deployment.
Some of the basic steps are;
Project planning, identifying the target audience and redesigning project, app development, testing and finally deployment.
Now, these are very basic steps and sometimes developers make mistakes in these simple steps which causes a huge problem for their and their client’s business.
In the mobile world where businesses like to give almost full control to their users on their device, it’s very important for application delivery team to have full control over their application as well.
But sometimes it does not happen and end result blows their mind. So in this blog, we are going to discuss few threats for your mobile application & how to make it more secure.
Unencrypted Local Storage
It is very standard for any application to store some amount of data for future access. But the real problem comes when something is stored and you are going to update the same data on the server. It might trouble you.
Let’s take Android’s local storage example to make it clear.
Android has SharedPrefs and SQLite storage and both are not automatically very secure. A simple shared preference storage would be something like this;
SharedPreferences sharedPreferences = getSharedPreferences(MY_PREF, MODE_PRIVATE);
SharedPreferences.Editor editor = sharedPreferences.edit();
editor.putString(“user_points”,“10000”);
editor.commit();
Now, this will save user level unencrypted. If the user is on rooted devices, a user can modify this value at any time. Because rooted devices are not used by normal users and this user definitely knows where to look for information on his/her device.
Before any modification:
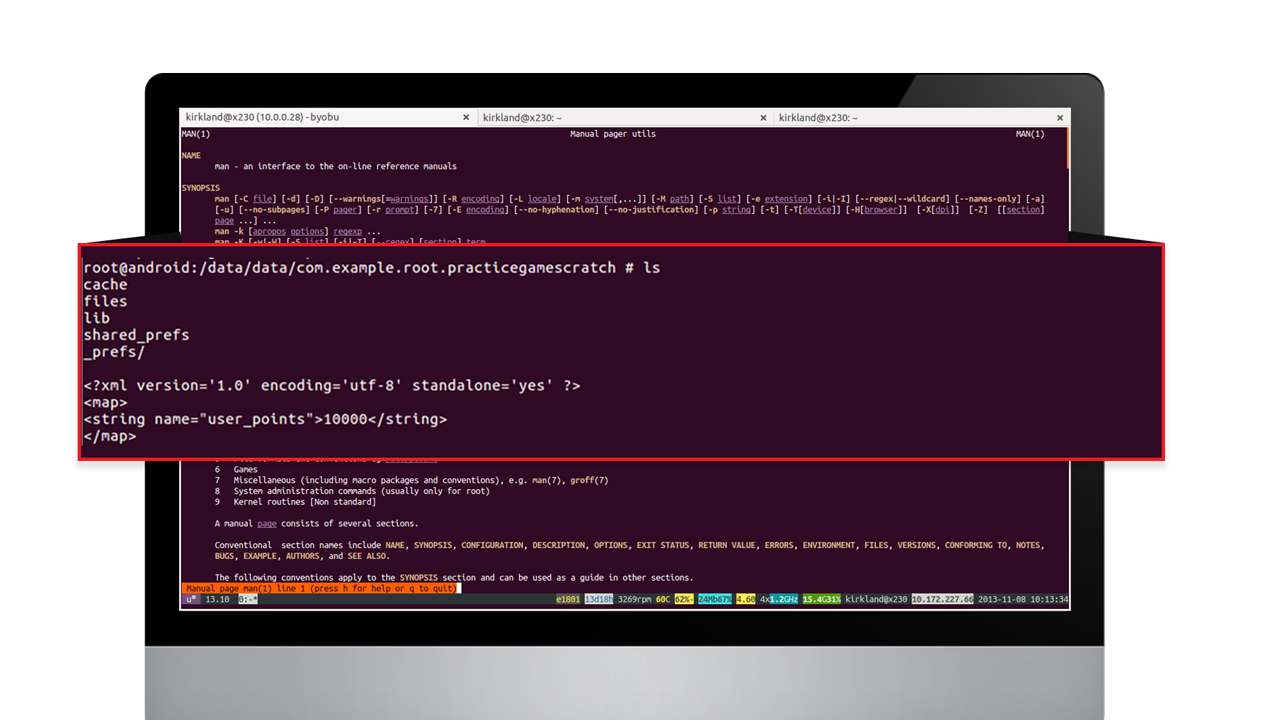
After modification:
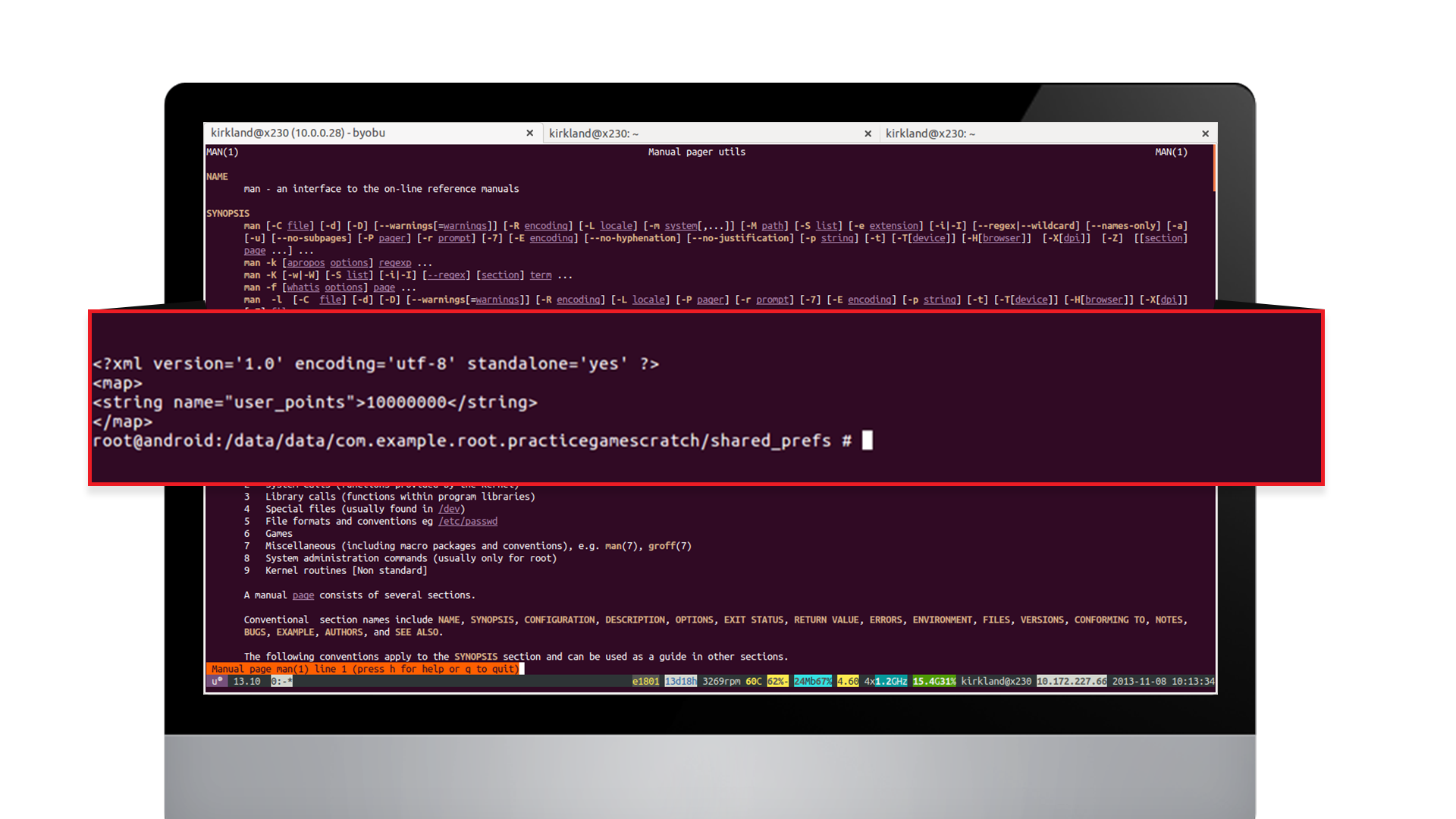
Weak API Access
In this case, it really doesn’t matter in which platform you are developing the application, if your API is not secure and if your application needs to communicate the server for accessing your business data, then this is a big issue. Let’s assume your server IP or API URL is in a geek’s hand & the first thing that geek would do with that is Denial Service Attack. If your server is unable to manage traffic, then your server will be down and you might lose real-time business information.
Imagine a scenario, when someone is completely dependent on your app and gets this kind of leak, how they are going to react. DDoS (Distributed Denial of Service Attack) is same, what GitHub faced last year & this was really bad for their business.

Basic but Important things to have on your server;
- SSL
- Always validate inputs from client
- Register a unique session for each client
Weak Client-side Control
This problem arises when we take inputs from the users and not validate that. It could be any junk data or you may also get SQL injection, which can break your logics both on the client side as well as server side.
Basic but Important things to have in your application;
- Input validation
- Checks for the connection that user is on (Remember it is not always the user who sacrifices his/her device, there are others who monitor them.)
- Check for connection certificate
Putting Sensitive Data at the Wrong Place
Sometimes developers forget that whatever they are writing has to be at its own safe place, and most dangerous mistake done by any programmer is putting the salt key (used for encryption) in resources (string) file.
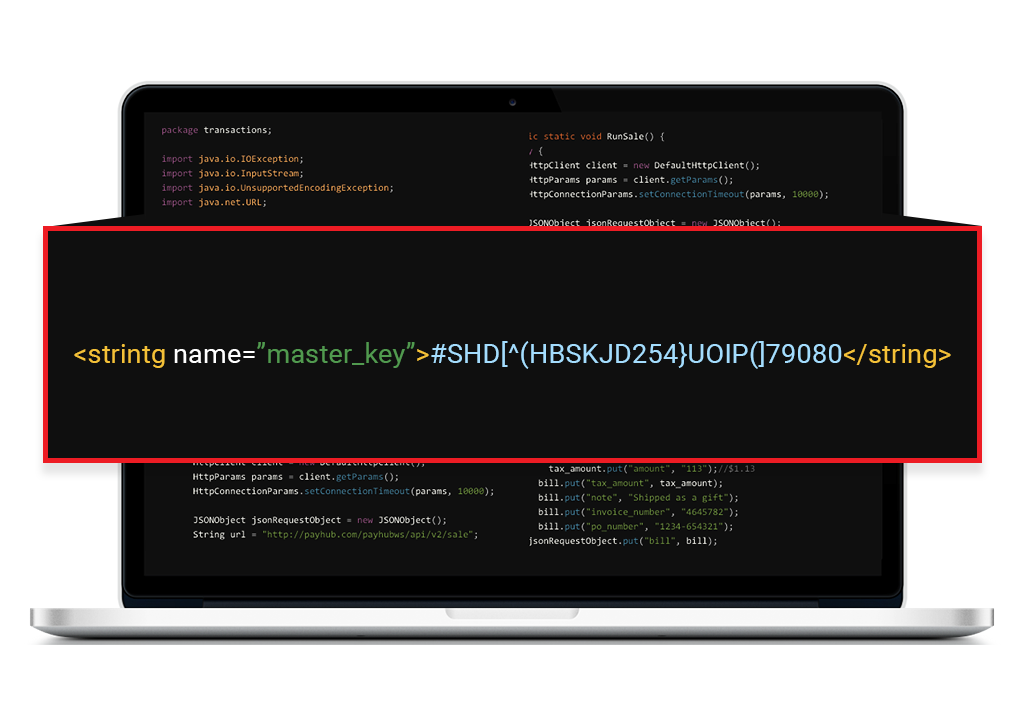
Now believe it or not but it is really very easy to extract apk file and keep all resource files exactly how it was during development stage in less than 2 minutes.
Code Security
The most important thing which should be addressed before deployment is applying reverse engineering and then breaking the logics.
If you have a project all set for deployment and you deployed that without confirming or validating your code security, then there are high chances that hackers can almost completely backtrace your compressed code.
Basic but Important things to be done for code security
- Code obfuscation
- Always prevent hardcoded strings
- Have almost all of your business logic on server and app
Unprotected Network Connection
Your mobile app APIs must be there on any server or cloud server. You should have network security measures in place to protect your business data and prevent unauthorized access. APIs and people who are accessing them should be verified to prevent protect sensitive information going to the server.
You can use containerization method to create encrypted containers for storing data securely. Your network engineer should ensure penetration testing is done and right data is flowing to the server. If you want to add an extra layer of security, you can go for database encryption and encrypted connections with a VPN (virtual private network), SSL (secure sockets layer) or TLS (transport layer security).
Weak BYOD Policy
If you are allowing your employees to use their own devices in your work place, they can access sensitive data on their phone. Sometimes it’s difficult for the IT dept. to regulate access. You can go for MDM (mobile device management) option. This can give employees the advantage to work anywhere, but also give your IT administrators all the control.
You can make devices “risk-aware” so that apps trying to make certain transactions are blocked from doing such activities. The app can be coded to detect and block certain transactions from rooted devices. Implement a VPN to generate a secure connection that’s less likely to be vulnerable to hackers listening in over an insecure network.
Conclusion
So this brings us to end of this blog, but there are many more problems that need to be taken care by delivery team and that’s what we do here at Apogaeis. We have a talented team dedicated to develop world-class business applications and IT security solutions.
We are here to help you in addressing your technological requirements so that you can concentrate more on your core business. Let’s collaborate to build game changing business apps which can transform your business. Contact Here with one of our expert & get a free consultation right away.
ALSO READ : “Mobile Application Development: Top 10 Factors to Consider”









